Target under attack

How supply chain digitalization helped hackers to exploit an air-conditioning firm and compromise operations of one of the US biggest retail companies.
Supply chain digitalization is a key component of many companies’ strategy to improve operational efficiency and competitiveness. Gains from digitalization are undeniable and go from basic inventory and logistics optimization to fully integrated digital networks that can predict and adjust the whole supply chain to changes on customer behavior. The more deeply integrated those networks are, the greater the company’s ability to build a supply chain that represents a true competitive advantage with potential to yield not only superior efficiency, but also enable new business models and revenue streams [1]. However, as a chain is only as strong as its weakest link, such integration can bring major risks and ultimately jeopardize a company’s ability to guarantee the safety of its own customers.
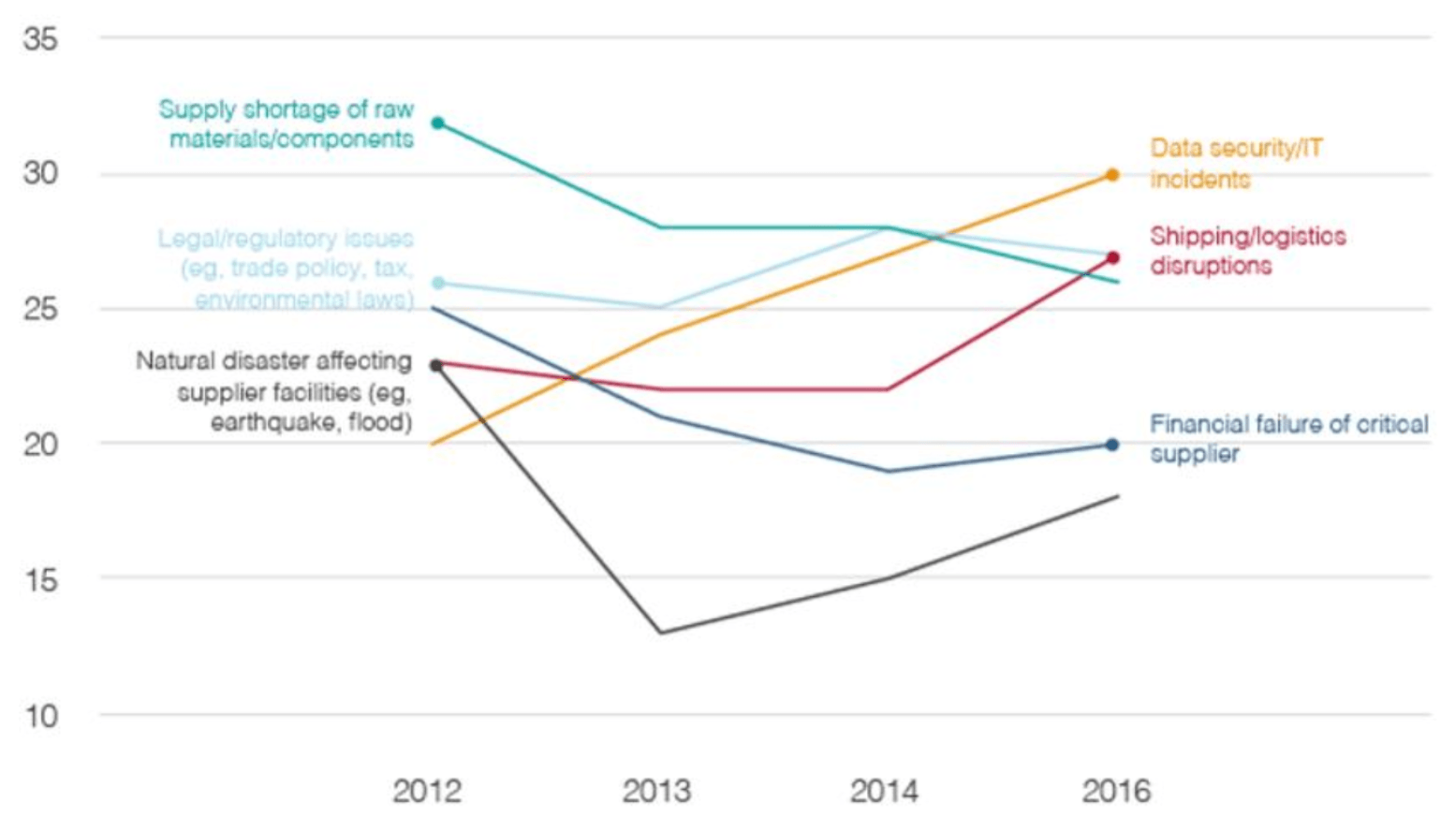
In December 2013, credit and debit card data of 40 million US customers and personal information of about 70 million breached from Target’s computers after hackers infiltrate into their databases through a corrupted system of a third-party air-conditioning firm [2,3,4]. Since then, data security and IT incidents have escalated to become a top concern of Chief Supply Chain Officers overcoming raw material shortages, and logistics disruptions [Figure 1].
Supply Chain Risks
% of respondents that are “very concerned” about each risk year-on-year
Figure 1 [5,6]
Soon after the incident, Target pledged to spend $100 million upgrading its security systems [3] and, as part of a more recent settlement [7], the company agreed to further enforce its compliance with Consumer Protection Statutes and deploy a comprehensive Information Security Program to protect personal information it collects from customers. Albeit huge investments on data security, protecting its systems from hacking continues to pose a great challenge to the company. So much so that 4 years after the major data breach, Target acknowledged that it continues to experience data security incidents [8]. As a result of the inability of companies to prevent such leaks, the number of US customers who experienced identity fraud increased 16% in 2016 to a historical record of 15.4M people [Figure 2] resulting on an estimated loss of $16Bi [9]. To minimize financial losses, many companies, including Target, have heavily relied on cyber-insurances that, although effective on compensating the economic aspect of the hacking, is a palliative solution that do not address the root cause of the problem.
US Customers Who Experienced Identity Fraud
In Millions
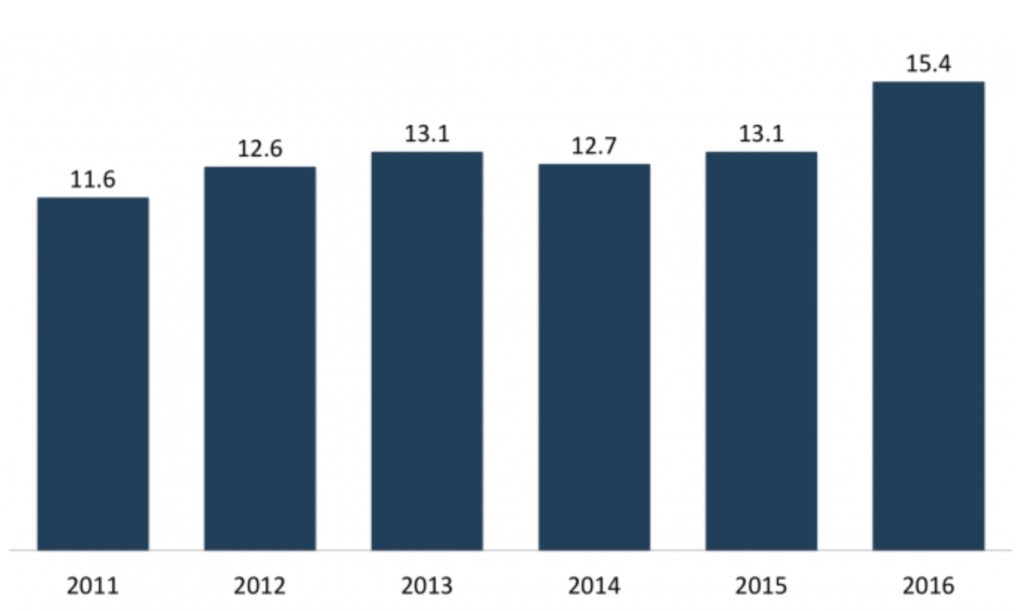
Figure 2 [9]
To deliver a higher level of security to its customers, Target’s management should focus on 3 key areas that are highlighted by many specialists [10] as foundations for a robust and reliable supply chain network.
First, Target’s supply chain needs to be thoroughly mapped and well understood so that all links of the network can have its weaknesses identified and adequately protected [Figure 3]. In addition to that, security systems and protocols must be established and tested to guarantee its efficacy once real threats are identified. A good example comes from the tech industry in which companies like Google run annual simulations of service disruption to evaluate how well teams go through response procedures and manage to keep the systems working and the data safe [11].
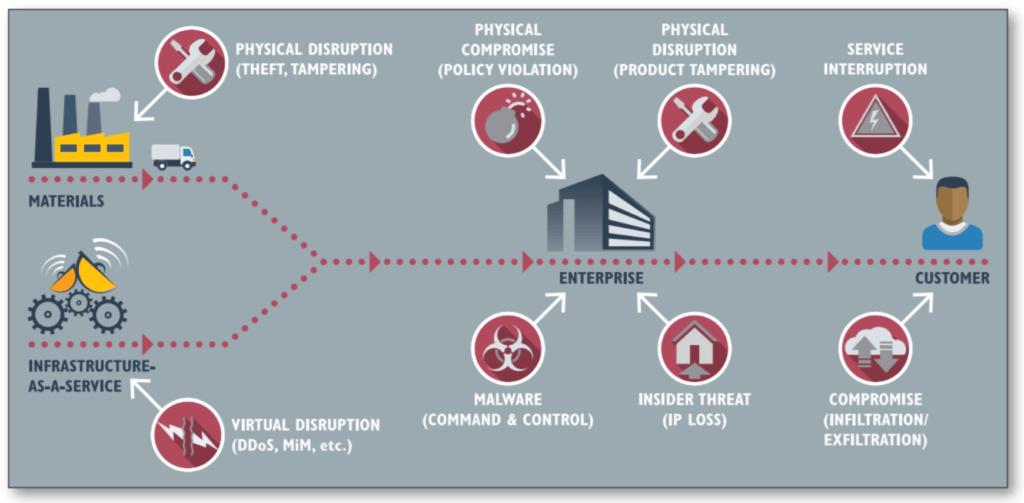
Figure 3: Anatomy of a Supply Chain Breach [12]
Second, the human factor needs to be addressed. Weeks before the 2013 breach, multiple malware alerts were ignored and prevention functionalities that could have mitigated the extension of the leak were turned off by administrators who were not familiar with the systems [4]. Therefore, a comprehensive training agenda needs to be put in place to educate all employees on basic security measures and also restrict access to sensitive data to a small and well qualified portion of the organization.
Finally, strong cryptography and multi-layer protection should be used to store and transmit sensitive data. Those measures add an extra layer of protection and avoid that, in case of a leak, any of the leaked information be ultimately used.
It is far from trivial, especially for retail companies, to put together such a complex system and many of them have relied on third-party cyber security and insurance firms to mitigate the risks. It is still open to debate, though, to which extend the responsibility for managing customer’s personal information should be transferred to third parties and how much retailers should rely on insurance companies to mitigate the implications related to data breaches. (727 words)
[1] strategy&, “Industry 4.0 – How digitization makes the supply chain more efficient, agile, and customer-focused,” PwC, 2016
[2] B. Krebs, “The Target breach, by the numbers,” May 2014, at https://krebsonsecurity.com/2014/05/the-target-breach-by-the-numbers/, accessed November 10, 2017
[3] E. Kvochko, R. Pant, “Why Data Breaches Don’t Hurt Stock Prices,” Harvard Business Review, March 2015
[4] X. Shu, K. Tian, A. Ciambrone, D. Yao, “Breaking the Target: An Analysis of Target Data Breach and Lessons Learned,” January 18, 2017, arXiv:1701.04940
[5] SCM World, “Future of Supply Chain surveys,” 2016
[6] SCM World, “Chief Supply Chain Officer Surveys,” 2012-14
[7] Attorney General of the State of New York, Bureau of Internet and Technology, Assurance no. 17-094, “Target Corporation Settlement,” May 8, 2017 at https://ag.ny.gov/sites/default/files/nyag_target_settlement.pdf
[8] Target Corporation, Form 10K – Annual Statement, January 2017
[9] Javelyn Strategy & Research, “2017 Identity Fraud Study,” February 1, 2017
[10] N. Lord, “Supply Chain Cybersecurity: Experts on how to mitigate third party risk,” July 27, 2017 at https://digitalguardian.com/blog/supply-chain-cybersecurity, accessed November 10, 2017
[11] Wired, “Google Throws Open Doors To Its Top-Secret Data Center”, October 17, 2012, at www.wired.com/2012/10/ff-inside-google-data-center, accessed November 12, 2017
[12] Combatting Cyber Risks in the Supply Chain – SANS Institute InfoSec Reading Room – September 2015 – page 2
[13] M. Riley, B. Elgin, D. Lawrence, C.Matlack, Bloomberg, “Missed Alarms and 40 Million Stolen Credit Card Numbers: How Target Blew It”, March 17, 2014, at https://www.bloomberg.com/news/articles/2014-03-13/target-missed-warnings-in-epic-hack-of-credit-card-data, accessed November 11, 2017



Really interesting paper!
We so often think about the benefits of supply chain digitization and you bring up a great point about a major risk. More information and more sharing naturally increases exposure of a company’s and customers’ information. To your point about who should be managing this risk, I believe Target and similar companies should begin investing in capabilities and not fully outsource to third party cyber-security and insurance firms. Strategic decisions at Target should be influenced by the associated security risk and if this this risk is fully managed by outside firms, it will not be appropriately factored into Target’s decision making. It can influence questions regarding vertical integration of supply chain, information that is recorded and tracked, who should have access to the data (e.g. consumer transaction data).
Great article.
I agree very much that we have been too oblivious about the downsides of adding another whole layer of potential digital disruptions to the supply chain (on top of the physical layer). That danger has been downplayed for too long, and now we – as corporations and as customers – are paying for this mistake via information breaches. It is stunning that Target – even though it had its first major data breach a while ago – is still struggling with measures to protect its information, and it highlights the security struggle that corporations face as they try to reap the benefits of a digital supply chain.
The second point of the set of mesaures you proposed stood out to me: The weakest link in the digital supply chain is – ironically – the human factor. Only with a comprehensive set of awareness trainings, digital “fire drills”, and constant reminders is it possible to minimize the risk of humans falling prey to hacking attempts made possible by phishing, social engineering and other means malicious hackers use.
Great post. For me, the real issue appears to be incentives for smaller players in the supply chain to cooperate with large players like Target. For a small player, a data breach is much less serious and the cost and inconvenience of upgrading their protections might not be justified in their minds, especially knowing that Target is heavily investing in cyber security insurance. What is the best way for Target to incentivize better security at its supply chain partners? One potential model could be premiums for players that reach certain levels of protection. Another could be for Target to set hard rules on the security requirements to even be a part of the Target supply chain.
The article was very intriguing as it points out the weaknesses and risks associated with technology and supply chain. As more and more companies move towards higher tech platforms and supply chain systems integrations, it is critical that they consider the security aspect. It would be interesting to see what segment of the industry plans sufficiently for up front Capex to be spent on systems and securities vs. bet on middle of the road quality and plan for reactive solutions down the road if needed. As a consumer who has been victim to not only target, but others similar to it (i.e. Blue Cross Blue Shields, Home Depot, etc.), I appreciated the article very much and depending on where I end up post HBS, I will have this in mind if I can influence the firm/company to improve their systems and protect both self and consumers.