How unwanted crowdsourcing can be the difference between life and death for the United States Department of Defense (DoD) and leads to Open Innovation in an insurgent war
This article explores the negative effects of undesired crowdsourcing and how it has been used in the battle field to yield catastrophic results.
In 2007 the United States Army suffered a direct attack in Iraq by a group of insurgents, who managed to destroy four new AH-64 “Apache Helicopters”. The attack was successful only because a group of American Soldiers uploaded photographs of the newly arrived helicopters to Facebook. The pictures that the soldiers took with their iPhone had geotagged the exact coordinates of the where the picture was taken. As Steve Warren, deputy G2 for the Maneuver Center of Excellence explains “Today, in pretty much every single smartphone, there is built-in GPS, (…) For every picture you take with that phone, it will automatically embed the latitude and longitude within the photograph.” (1)
Similar events have occurred where United States Service Members unwillingly have given out their unit location by commenting on Facebook and Twitter events that occur in the day to day activities of their deployment. The comments and posts are taken by the enemy in Iraq, Afghanistan, and Syria to locate, evade, and harm the mission of the Department of Defense. (2)
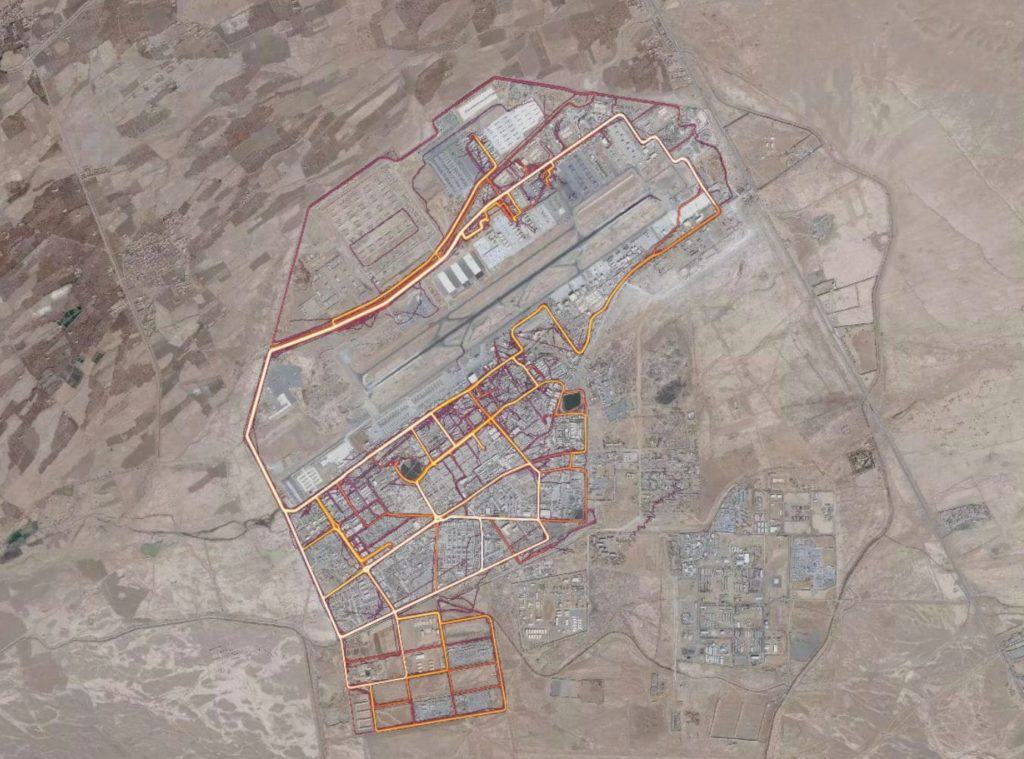
Most recently as of January 2018, the jogging platform Strava is capturing sensitive information of Service member locations, size of the force, and even outer perimeter movements and patrol routes, by tracking the fitness devices that Service members use, such as Fitbit and Jawbone (Exhibit 1 shows a map of Kandahar Airfield Afghanistan produced by Strava Labs) (3). This unwilling crowdsourcing can prove disastrous for the covert missions necessary to win the insurgency wars in the middle east, as they provide to the insurgent’s valuable real time information on military capabilities, troop placements, and patrol routes, all of which need to remain secret to ensure the success of the mission. This information can also lead to the loss of service members by coordinating precise attacks based on the information gathered. (1) (2) (3)
So far, the Department of Defense has been very vigilant regarding the undesired crowdsourcing by introducing very strict policy regarding the use of Social Media by service members. It also has created several training programs that Service members need to take, both in garrison and while deployed, that highlight the consequences of poor social media use and the military punishments that are associated with it. (4) The DoD has also introduced military reprimands for service Members who disseminate information via Social Media, yet as the landscape of technology evolves the new military policy must keep up to date to ensure that vital information is not shared with the enemy. Currently the DoD has not created a policy regarding the use of jogging technology while in a deployed location as they are analyzing ways to prevent the unwanted outsource data to be shared with the public. (5)
The United States has also learned from the enemy and since has utilized social media to locate and eradicate the enemy insurgency, as was the case in 2015 when an ISIS commander used Twitter to discuss some new organizational changes in the ISIS chain of command, the United States Air Force responded with three Joint Direct Attack Munition (JDAMs) in less than 20 minutes (6). Currently the DoD has a group of cyber technology experts monitoring the social media account of multiple terrorist organizations to discover unwanted information that their members post on social media.
As technology continues to advance the use of geolocation will be more prevalent than ever, the DoD needs to find new ways to protect its members from undesired crowdsourcing by doing something more than issuing anti use policy. As demonstrated with tangible events a simple undesired mistake by a service member can lead to mortal consequences, for these reasons the DoD should invest in new technology that disables or alters the Geolocation GPS device in personal devices, thus ensuring that the enemy will not be able to benefit from undesired crowdsourcing such as a picture and jogging devices. Until that new technology is developed the DoD should not only focus its energy in finding enemy locations but should also use its resources to monitor deployed locations to prevent a simple mistake by service members that could lead to a loss of life or equipment.
As new technology is introduced to the consumer space, how can consumers protect their privacy, when unwillingly the new technology they take for granted has a method of crowdsourcing for companies without users noticing? Is privacy dying as a trade off with new technological advancements?
References
Military.com. (2018). Insurgents Used Cell Phone Geotags to Destroy AH-64s in Iraq. [online] Available at: https://www.military.com/defensetech/2012/03/15/insurgents-used-cell-phone-geotags-to-destroy-ah-64s-in-iraq [Accessed 13 Nov. 2018].
Singer, E. (2018). War Goes Viral. [online] The Atlantic. Available at: https://www.theatlantic.com/magazine/archive/2016/11/war-goes-viral/501125/ [Accessed 13 Nov. 2018].
Timberg, L. (2018). U.S. military reviewing its rules after fitness trackers exposed sensitive data. [online] Washington Post. Available at: https://www.washingtonpost.com/world/a-map-showing-the-users-of-fitness-devices-lets-the-world-see-where-us-soldiers-are-and-what-they-are-doing/2018/01/28/86915662-0441-11e8-aa61-f3391373867e_story.html?utm_term=.caac02a1fab8 [Accessed 13 Nov. 2018].
Timberg, L. (2018). U.S. military reviewing its rules after fitness trackers exposed sensitive data. [online] Washington Post. Available at: https://www.washingtonpost.com/world/a-map-showing-the-users-of-fitness-devices-lets-the-world-see-where-us-soldiers-are-and-what-they-are-doing/2018/01/28/86915662-0441-11e8-aa61-f3391373867e_story.html?utm_term=.caac02a1fab8 [Accessed 13 Nov. 2018].
Walbert Castillo, C. (2018). U.S. bombs ISIS using social media intel – CNNPolitics. [online] CNN. Available at: https://www.cnn.com/2015/06/05/politics/air-force-isis-moron-twitter/ [Accessed 13 Nov. 2018].
Washington Post. (2018). U.S. military reviewing its rules after fitness trackers exposed sensitive data. [online] Available at: https://www.washingtonpost.com/world/the-us-military-reviews-its-rules-as-new-details-of-us-soldiers-and-bases-emerge/2018/01/29/6310d518-050f-11e8-aa61-f3391373867e_story.html?utm_term=.562a9437aa73 [Accessed 13 Nov. 2018].
www.army.mil. (2018). Geotagging poses security risks. [online] Available at: https://www.army.mil/article/75165/geotagging_poses_security_risks [Accessed 13 Nov. 2018].



Very interesting take on the unintended consequences of technology. My concern is with our reciprocation of the enemy’s tactics – is this data reliable enough to launch US attacks when weighed against the risk of collateral damage? I would be concerned that such geo-tagging could be manipulated, leading us to attack the wrong places, possibly leading to civilian casualties and subsequently hurting the cause.
Excellent and thought provoking article. To the comment above and to the article, I would argue that geo-tagging is not and should never be used in a vacuum. It is rather another intelligence breadcrumb used in a puzzle for targeting needs. Units should always be sensitive to collateral damage, no matter how sure the information.
I would take the final assertion a step further and say, with the proven depression that comes from excessive social media use, and the obvious issues with troops revealing mission critical information in online posts, is there any downside to forbidding the use of personal smart phones all together in deployed zones?
I completely agree with this article – thanks for sharing. The DoD must do better at managing the telecommunications of its Soldiers in the battlespace – mostly by beefing up its current communication structure to be more useful for the troops on the ground. I remember vividly how many convoys, airdrops, and other logistics missions were coordinated via WhatsApp in the theater that I operated in – simply because our issued equipment was far inferior and it was easier to communicate over the phone. This was nerve-wracking for senior leadership as potential adversaries had the ability to listen in to many of our communications. We need to ensure that our own equipment is a more viable alternative.
Also – another interesting story on geotagging – in the early days of the War in Ukraine, it was widely known that Russian soldiers were operating in Ukraine (contrary to what their government was suggesting) based on multiple Instagram geotags of Russian artillery soldiers, who were bored in their vehicles posting on social media!
Great article and highly relevant in today’s context. Thanks for sharing a perspective on the darker side of crowdsourcing and open-innovation. To address your question, I believe that it is critical for users of any type of popular social media technologies to be educated about their privacy risks. Education is truly the first line of defence. This type of education can come in many forms – formal training by the government/company, or self-guided training through online videos that teach users the type of data social media companies collect (e.g., location data, timestamp data, other personal data).