Can the United States Coast Guard prevent cyberattacks from sinking our connections to global supply chains?

New threats emerge with the digitalization of the maritime supply chain. Can the United States Coast Guard stop the rising tide of cyberattacks?
On 24 October 2017 the United States House of Representatives passed H.R. 3101 Strengthening Cybersecurity Information Sharing and Coordination in Our Ports Act of 2017 [1]. The bill was introduced in response to the June 2017 global cyberattack that shut down the Port of Los Angeles’ largest terminal [2] via infection of shipping company Maersk (who leases the terminal) by the NotPetya worm [3]. The attack stalled 76 of Maersk’s global port terminals in total [4]. Parent corporation A.P. Moeller-Maersk estimated that the cyberattack would cost the company $200m – $300m [5].
The United States Coast Guard (USCG) is charged to protect the maritime transportation system (MTS) from both physical and cyber- attacks. The MTS handles over $1.3 trillion in cargo through approximately 360 ports annually and links the United States to global supply chains. Figure 1 shows the top 25 water ports by cargo container volume. Digitalization of the maritime sector (from ship navigation to port operations) has increased efficiency but introduced the crippling threat of cyberattacks [6]. As shown just by the impact of the cyberattack on Maersk, failure of the MTS due to cyberattack could be catastrophic for the United States.
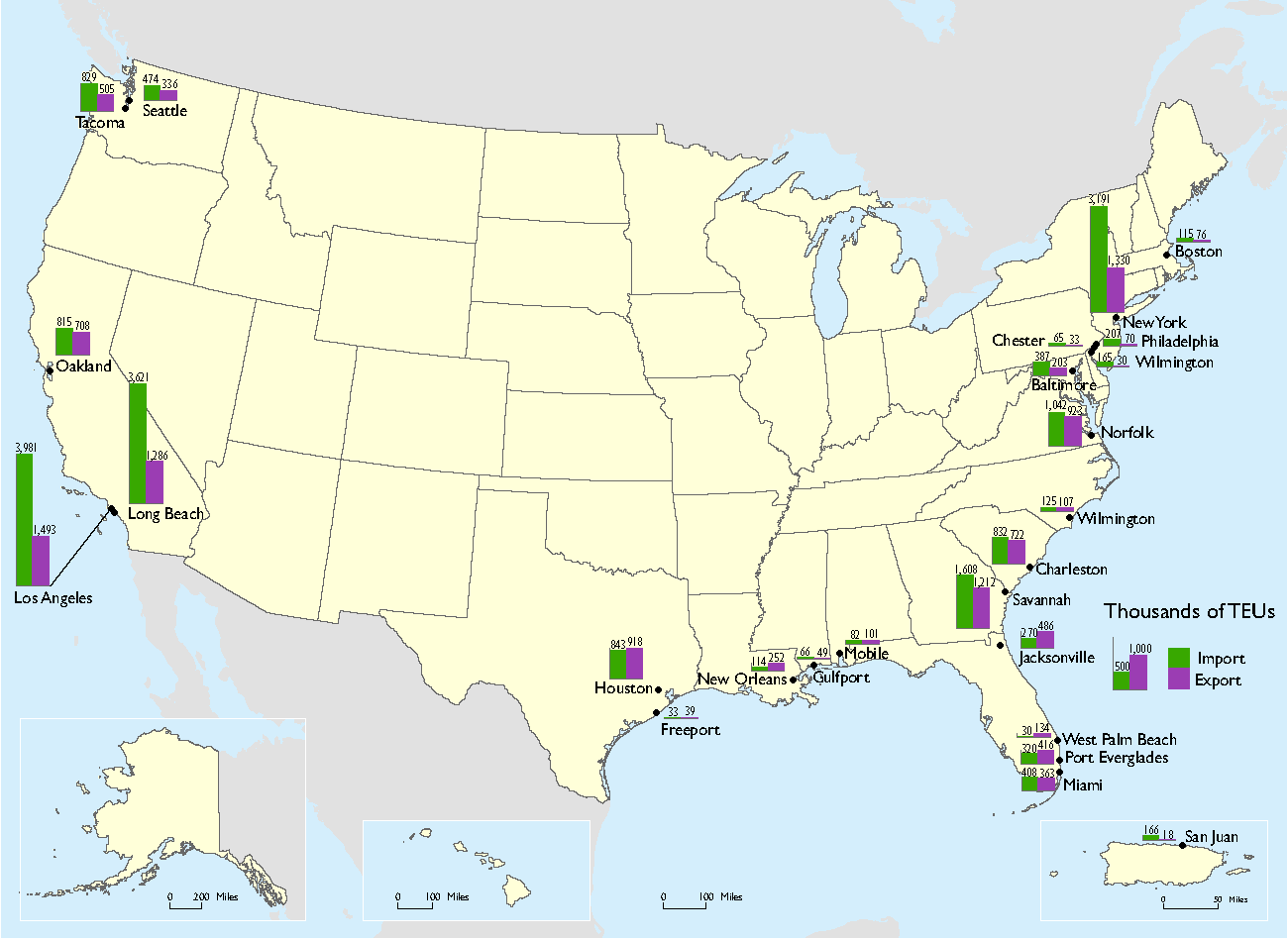
Source: U.S. Department of Transportation, Maritime Administration, 2000-2015 U.S. Waterborne Container Trade by U.S. Customs Port, derived from IHS Maritime, Port Import/Export Reporting Service (PIERS), available at https://www.marad.dot.gov/resources/data-statistics/ as of October 2017. (accessed November 2017 from https://www.bts.gov/topics/maritime-and-inland-waterways)
The U.S government is aware of these risks. In 2015 the USCG released a 10-year cyber strategy that includes a strategic priority to protect infrastructure (e.g., the MTS) through two goals: 1) “risk assessment – promote cyber risk awareness and management” and 2) “prevention – reduce cybersecurity vulnerabilities in the MTS.” Goal 1 revolves around improving risk assessment tools and information sharing with the maritime industry and government stakeholders. Goal 2 is based on establishing vessel/facility cybersecurity standards and personnel training requirements [6]. Essentially, the USCG strategy to protect the MTS is about raising awareness and understanding of the cyber threat for both participants and stakeholders. USCG seeks to build a culture of cyber risk management that is analogous to safety culture [7].
Although the 2015 cyber strategy does not provide details on execution timing, recent USCG actions and communications appear to be in line with achieving the stated goals. For example, in line with goal 1, the USCG published a cybersecurity series in the Coast Guard Maritime Commons (their blog for maritime professionals) for national cybersecurity awareness month (October) that discusses cyber incidents, poses questions, and provides links to important guidelines, standards, and frameworks [8]. In line with goal 2, the USCG collaborated with the International Maritime Organization (IMO) to write Guidelines on Maritime Cyber Risk Management [7] and released a draft of NVIC 05-17 Guidelines for Addressing Cyber Risks at Maritime Transportation Security Act (MTSA) Regulated Facilities for comments [9].
Is the USCG culture-based approach to cybersecurity (and hence MTS protection) valid? I think so. First, given that an organization can be exposed to malware by one person clicking one link in an email, it seems clear that enforcing safe cyber behavior at all levels is paramount. Experience in the oil and gas sector taught me the importance of strong safety cultures for enforcing safe behaviors. Hence, if cybersecurity is analogous to safety, which it seems to be, then this approach will be effective. Second, frequent communication via the Coast Guard Maritime Commons should help industry users digest the vast array of guidelines, standards, and cyber security practices scattered across various groups and agencies. Third, development of guidelines, especially through international organizations like IMO should help ensure compliance by international shipping companies (e.g., Maersk is Danish) in utilizing the MTS securely.
Still, the USCG approach to protect the MTS from new digital threats could be improved by two additional actions. First, USCG should consolidate critical information in one location and simplify the message. Searching for maritime cybersecurity guidance was a journey through lengthy manuals and regulatory documents across various agency sites. Clear and more easily accessible information should help to improve awareness and education. Prominent display of cyberattack statistics would also help to enforce the message. Second, USCG should require mandatory rapid reporting of cyber incidents to enhance information sharing and damage mitigation. Even new legislation such as H.R. 3101 only requires voluntary reporting of maritime cybersecurity incidents [1]. Unreported attacks are missed learning opportunities.
In conclusion, digitalization of maritime supply chains (and the MTS) has created new cyber threats for the USCG, the nation, and the shipping industry to battle. Discussion of how the USCG can best protect the MTS (and the nation’s maritime supply chains) from cyberattacks raises many questions. Should the USCG go on the cyber offensive? Would mandatory cyberattack reporting requirements sacrifice the right to privacy?
(742 words)
References
[1] Summary of H.R. 3101 “Strengthening Cybersecurity Information Sharing and Coordination in Our Ports Act of 2017,” Congressional Research Service, 24 October 2017
https://www.congress.gov/bill/115th-congress/house-bill/3101
[2] “House Passes Torres Bill to Address Port Cybersecurity Threats”, 24 October 2017
https://torres.house.gov/media-center/press-releases/house-passes-torres-bill-address-port-cybersecurity-threats
[3] J. Leovy and A. D’Angelo, “Maersk’s L.A. port terminal remains closed after global cyberattack,” LA Times, 29 June 2017
http://beta.latimes.com/business/technology/la-fi-maersk-cyber-attack-20170629-story.html
[4] R. Milne, “Maersk CEO Soren Skou on surviving cyber attack,” Financial Times, 13 August 2017
https://www.ft.com/content/785711bc-7c1b-11e7-9108-edda0bcbc928
[5] R. Milne, “Moler-Maersk puts cost of cyber attack at up to $300m,” Financial Times, 16 August 2017
https://www.ft.com/content/a44ede7c-825f-11e7-a4ce-15b2513cb3ff
[6] United States Coast Guard Cyber Strategy, United States Coast Guard, June 2015, accessed November 2017. http://www.overview.uscg.mil/Portals/6/Documents/PDF/CG_Cyber_Strategy.pdf?ver=2016-10-13-122915-863
[7] K. Kuhn, “Nat’l Cybersecurity Awareness Month – Shipboard cyber risk management,” Coast Guard Maritime Commons, 9 October 2017
http://mariners.coastguard.dodlive.mil/2017/10/09/1092017-natl-cybersecurity-awareness-month-shipboard-cyber-risk-management/
[8] B. Link, “Nat’l Cybersecurity Awareness Month – Five key cyber questions and challenges facing the maritime industry,” Coast Guard Maritime Commons, 30 October 2017
http://mariners.coastguard.dodlive.mil/2017/10/30/10302017-natl-cybersecurity-awareness-month-five-key-cyber-questions-and-challenges-facing-the-maritime-industry/
[9] Y. Barril, “Nat’l Cybersecurity Awareness Month – October is National Cyber Security Awareness Month,” Coast Guard Maritime Commons, 2 October 2017
http://mariners.coastguard.dodlive.mil/2017/10/02/1022017-october-national-cyber-security-awareness-month/
USCG Cyber Command Logo: http://allhands.coastguard.dodlive.mil/2013/10/30/how-does-coast-guard-cyber-security-keep-our-everyday-systems-operating-safely/uscg-cyber-command/



You touch on some interesting elements of culture and transparency to help improve their cybersecurity measures. There are two learnings from TOM this year that seem to apply here. The first is this understanding that mistakes (and cyber attacks) will happen. An organization is stronger when it is prepared for the failure to occur, not just focused on preventing it. With the rapidly advancing pace of cyber attacks, these organizations need to “think around the corner” and assume that an attack will happen at some point. Secondly, you mention at the end that “unreported attacks are missed learning opportunities,” which mirrors the no-blame culture we saw at Toyota. If people cover their mistakes, others don’t learn how to prevent those going forward and the organization is not strengthened. This, as you point out, can come down to culture. If the culture of the organization can somehow encourage people to share their failures and learning mistakes, similar to how Toyota managed this in their production processes, the USCG could be stronger. However, changing to a no-fault culture can take years in an org where there is low management turnover.
This was an interesting read and I fully agree with Joe’s comments above. I believe a successful cyber attack is a question of when not if it will happen. I agree with your assessment that the USCG needs to consolidate training materials, but I do not believe this is enough. Just because information is available, does not mean individuals will utilize that information. Many companies are undergoing cyber security training by launching their own phishing emails to employees. If employees click on the link, then they are taken to a very short training module to learn more about protecting their organization against cyber security. Additionally, in the same way that organizations require all employees to participate in fire drills, I believe they should create responses for cyber attacks and train all employees on the proper responses.
Thanks for an interesting read! It’s a topic that I’ve never given much thought to and I appreciate you shedding some light on it. I’m curious how you interpret “going on the offensive” for the USCG. I can’t imagine them using offensive cyber weapons but I believe there is absolutely room for the USCG to be more proactive. Building on Steve’s point about training employees on proper responses, I think the USCG could also incorporate “cyber inspections” into its routine checks on equipment and training. Last fall, I had the opportunity to observe a USCG inspection of a chemical tanker in the Port of Houston. While the USCG team diligently inspected everything from the fuel storage systems to ship logs to the crew’s knowledge of regulations, there wasn’t a point where they talked about computer networks or the crew’s understanding of cyber threats. This seems like a relatively simple change that could do a lot to ensure cyber training and regulations are reaching the lowest ranking crew members, especially considering the national and cultural diversity.
Thanks for a fascinating – if slightly terrifying – post! I’m thinking about this from a TOM perspective as a quality control problem. I wonder if the Cost Guard might invest more energy earlier in the process. Is there a way they could share some of the ship management tools that they have access to which potentially go though more rigorous security vetting? Given that shipping attacks are a serious national security concern, I wonder if they could help companies diagnose the root causes of security gaps, akin to the work of the NTSB. I also think there are opportunities for the Coast Guard to test security vulnerabilities. One extreme idea is that the Coast Guard could serve as a “Red Team” purposely attacking the digital infrastructure in an effort to uncover potential vulnerabilities before our adversaries. These areas of risk and potential mitigation could then be shared with the relevant parties.